CSC 361 Cybersecurity for Future Presidents
Future Presidents will need to understand the science, technology, and human considerations behind cyber security well enough to make informed decisions when provided advice and options for action. By adopting the perspective of training future Presidents, this course aims to help all students (whether or not they later seek leadership positions in government or industry) to understand cyber security, privacy, and intellectual property issues from technical and social perspectives. It assumes a basic familiarity with computers including use of modern desktop, mobile and web-based platforms. It is designed for students who have an interest in thinking critically about how technology and cyber security may affect individuals, groups, and organizations in 20-30 years. Government by the people depends on a citizenry that understands the issues their leaders must address. This course will provide students the tools to understand and evaluate the actions of future leaders in the area of cyber security.
Learning Objectives
At the end of the course, students should:
-- Technical Foundations:
Explain fundamental concepts of computing and cyber security, including information theory, computability, cryptography, authentication, access control, information flow, anonymity, privacy, accountability, how vulnerabilities arise and how attacks work.
-- Policy Foundations:
Explain relevant laws, policies, societal and market forces that will continue to shape policy surrounding cyber security and privacy.
--Critical Thinking:
Be able to apply their understanding of technology and policy to assess critically arguments put forth in favor of alternative policy positions.
Methods of Assessment
Students will be assessed in four ways: through class participation and homework assignments, including participation in classroom debates, (40%), on a mid-term exam (30%) and a final exam (30%).
Rather than providing extra credit work - we will count the final exam as 40% and the midterm as 20% for any student who does better on their final exam than on their mid-exam. This should incentivize students to learn the materials they missed on the midterm.
Exercise Late Policy
Your exercise grade will be deducted a certain percentage based on the following guidelines:
--10% When submitted after the due date/time BUT before the exercise is reviewed in class.
--25% when submitted after exercise review in class BUT before exercise solutions posted in Canvas.
--50% when submitted after exercise solutions posted in Canvas.
Text Book
Primary: Kernighan, B. D is for Digital. DisForDigital.net, 2011.
Supplementary: Anderson, R. Security Engineering. Available at http://www.cl.cam.ac.uk/~rja14/book.html
Instructors
-- Primary Instructor: Carl Landwehr - [email protected]
-- Supporting: Aparna Das - [email protected] and Dave Voorhees - [email protected]
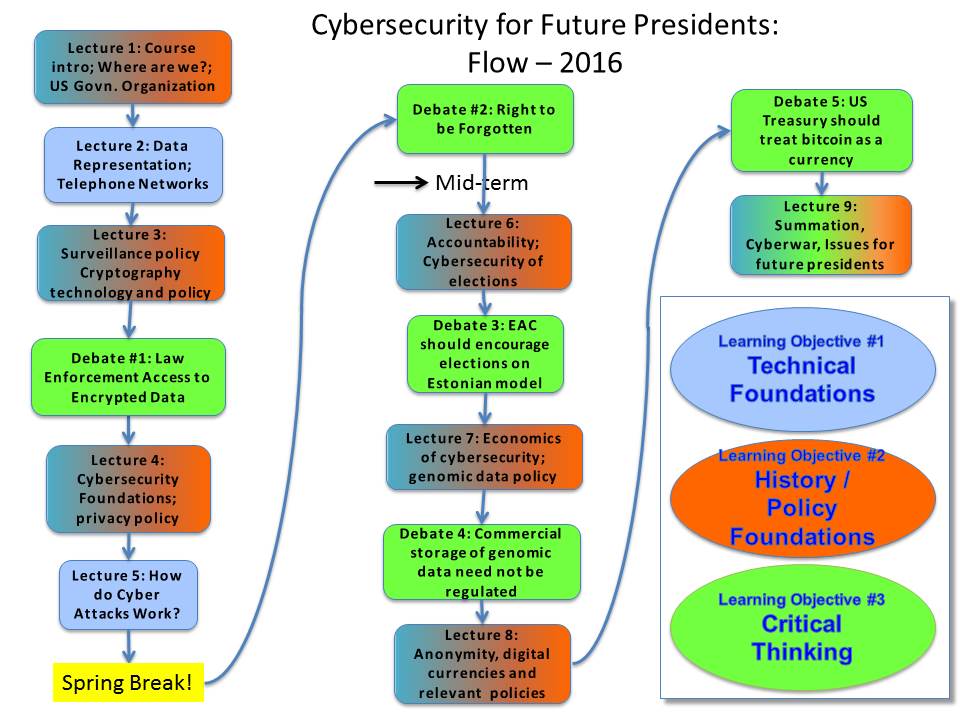
Weekly Schedule
See
below for course flow graphic.
| Week |
Topic |
Lecture Slides |
Assignments |
| 1 |
Introduction to the course. Where are we today? US Government Organization. |
PPT | PDF |
A1 |
| 2 |
Data Representation. How telephone networks work? Wiretapping history & policy. |
PPT | PDF |
A2 |
| 3 |
Surveillance policy, Cryptography technology and policy. |
PPT | PDF |
A3 |
| 4 |
Debate #1:Crypto backdoor for LE access |
PPT | PDF |
A4 |
| 5 |
Security Foundations. Privacy policy background |
PPT | PDF
|
A5 |
| 6 |
How Cyber attacks work. |
PPT | PDF |
A6 |
| 7 |
Debate #2. Right to be forgotten. Midterm review. |
PPT | PDF |
A7 |
| 8 |
Accountability. Intro. to eVoting. |
PPT | PDF |
A8 |
| 9 |
Debate # 3:Internet elections like Estonia. Extra time on Scams, Metcalfe's Law, in-band/out-of-band comms |
PPT | PDF |
A9 |
| 10 |
History of technology and economics of cybersecurity, genomic privacy background |
PPT | PDF |
A10 |
| 11 |
Debate #4:commercial genomic databases provide adequate protection. |
PPT | PDF |
A11 |
| 12 |
Anonymity, digital currency, digital currency attempts, bitcoin and blockchain, relevant policy/legislation |
PPT | PDF |
A12 |
| 13 |
Debate #5: Treasury should treat bitcoin as currency, not property. Extra time: financial cybersecurity? |
PPT | PDF |
A13 |
| 14 |
Summation lecture. Issues for future Presidents. Cyberwar, surveillance, big data. Course review & farewell. |
PPT | PDF |
Study for final |
Files for Course
 |
NSF Award #1500033 DGE Division of Graduate Education SaTC-EDU: EAGER: INCUBATE - INjecting and assessing Cybersecurity edUcation with little internal suBject mATter Expertise |